OpenShift Routes Virtual Service Configuration
Starting with Avi Vantage 20.1.1, the Kubernetes/ OpenShift cloud is no longer supported.
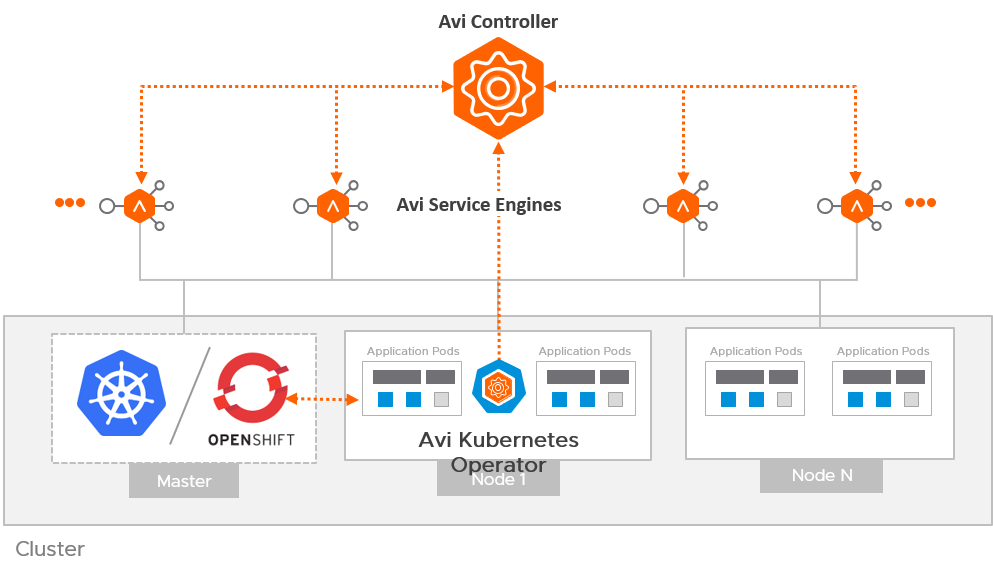
The Avi Vantage platform integration with OpenShift/Kubernetes introduces a redesigned architecture involving a new operator called Avi Kubernetes Operator (AKO). The components of the Avi Kubernetes integration is as shown below:
To facilitate deployments across multiple OpenShift/Kubernetes clusters, the Avi Multi-Cluster Kubernetes Operator (AMKO) is introduced.
-
For new Kubernetes/ OpenShift installations, deploy Avi Kubernetes Operator (AKO) and Avi Multi-Cluster Kubernetes Operator (AMKO).
-
To continue using the OpenShift/Kubernetes cloud type, use the Avi Vantage 18.2.x line of releases.
For Avi Vantage Release and End of Support information, click here.