PingAccess Agent Configuration
Overview
NSX Advanced Load Balancer (formerly known as Avi) administrators can use Ping Identity’s PingAccess Agent to control client access to a virtual service.
How It Works
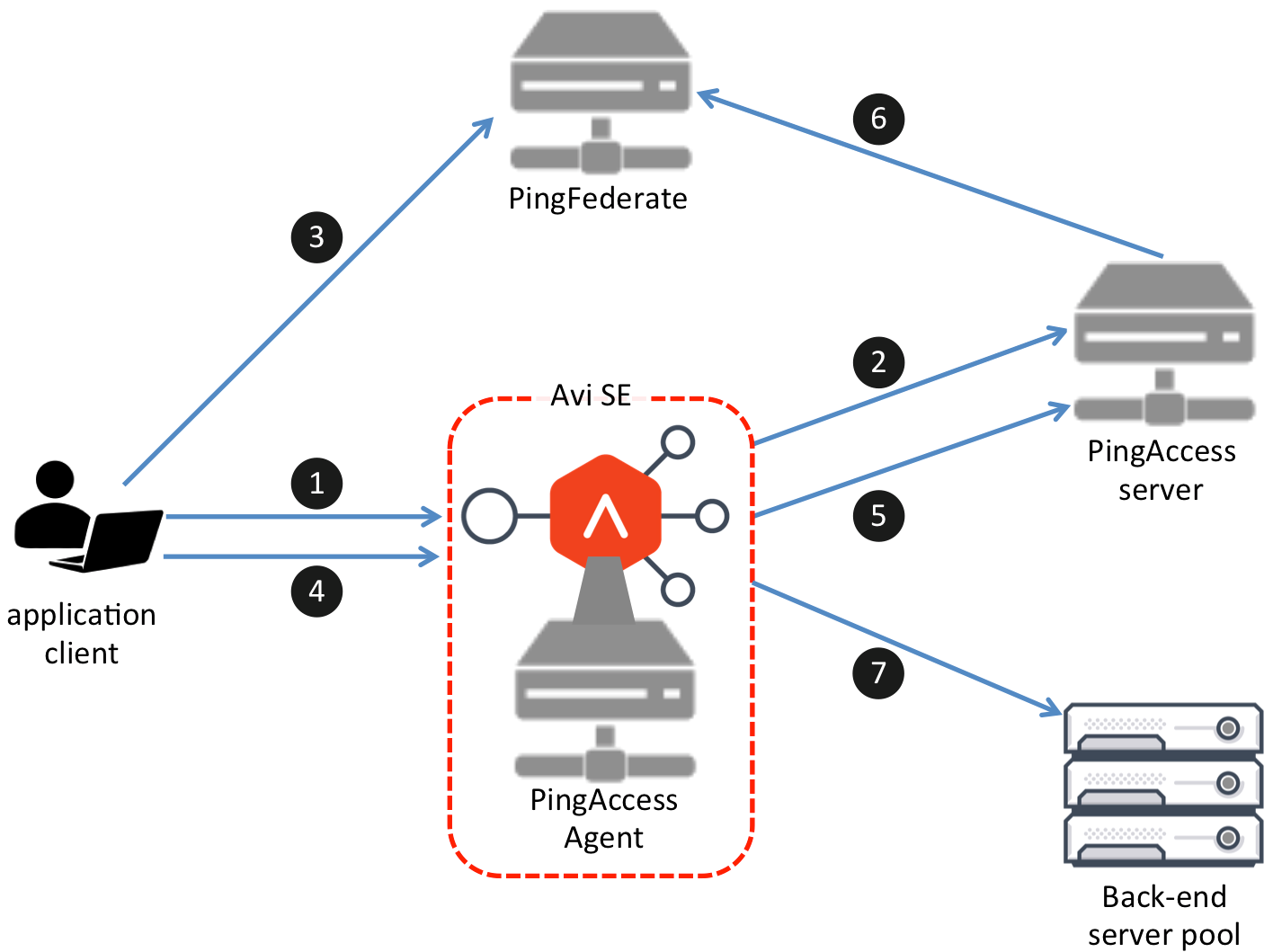
This scenario assumes the client has not yet authenticated itself, i.e., has no cookie that would indicate it had previously logged into PingFederate.
- The client accesses the virtual service running on the SE. For this virtual service, the SE is configured to check with the PingFederate Agent for both authentication and authorization purposes. If the Agent determines the client has already been authenticated, it skips to point 5.
- Assume the PingAccess Agent has no record in its cache of authenticating this client. It directs NSX Advanced Load Balancer to temporarily park the request. After this,
- The PingAccess Agent asks the PingAccess Server for instructions.
- The PingAccess Server checks its URL policy and determines that access has been requested to one of its protected resources. It responds to the PingAccess Agent with a code the SE passes back to the client without interpreting it. The client will interpret the code as a redirect for the purpose of establishing a session with PingFederate.
- On receiving the code, the client sends a request to PingFederate. If PingFederate determines the client should be validated, it creates the session.
- The client is then redirected back to the resource, i.e., back to the Avi SE. This time the request includes a cookie identifying it as a legitimate user. The PingAccess Agent caches the client’s authentication information.
- The PingAccess Agent recognizes the client has been authenticated.
- Once again, while NSX Advanced Load Balancer has parked the request, the PingAccess Agent asks the PingAccess Server for authorization instructions.
- PingAccess Server checks its URL policy and determines that it is a protected resource. It checks the session token, determines that it is valid, and replies to the Agent that the client is authorized to access the resource.
- If session revocation is enabled, the PingAccess Server checks and updates the central session revocation list maintained by PingFederate. If the session is valid, the Agent is instructed to re-establish identity HTTP headers.
- The SE passes the authenticated and authorized request through to a selected back-end server.
Note: All request logs for a virtual service configured with PingAccessAgent will contain evidence of the PingAccess subrequests via which the PingAccess Agent obtains the information it needs. Such log entries include a “PaaLog” string for easy identification.
Configuring a Virtual Service to Use PingAccess Agent
Follow the steps mentioned below:
- Configure the PingAccess Agent Profile
- Configure the Auth Profile
- Configure the SSO Policy
- Bind the SSO Policy to the virtual service.
<a name=agent”></a>
Configuring the PingAccess Agent Profile
- Navigate to Templates > Profile > Security > PingAccess Agent Profile.
- Click on Create.
- Enter a Name for the profile.
- Either paste the contents of PingAccess Agent’s agent.properties file or click Import to select the file and upload.
Note: The PingAccess administrator will have used the PingAccess UI to download to his workstation’s file system from the PingAccess Server a properties file containing the shared secrets needed by the SE’s PingAccess Agent. Its file name has the form
<agent_name>_agent.properties. Placing the file in the administrator’s current directory, it is possible to refer to it using a simple pathname comprised solely of the file name,AviAgent_agent.properties.
- Click Save.
Note: The properties of the PingAccess Agent cannot be edited once it is installed. Instead, delete the previous Agent and upload a new one.
<a name=profile”></a>
Configuring the Auth Profile
- Navigate to Templates > Profile > Security > Auth Profile.
- Click Create.
- Enter the Name of the Auth Profile.
- Select the Type as PingAccess.
- Under PingAccess select the PingAccess Agent Profile.

- Click Save.
<a name=sso”></a>
Configuring SSO Policy
- Navigate to Templates > Profile > Security > SSO Policy.
- Click Create.
- Enter the Name of the SSO Policy.
- Select the Type as PingAccess.
- Under Authentication select Auth Profile created with PingAccess as Type.

- Click Save.
<a name=vs”></a>
Binding the SSO Policy to a Virtual Service
- From a New Virtual Service screen or Edit Virtual Service screen, navigate to Step 2: Policies > Access.
- Select PingAccess as the Access Policy.
- Select the SSO Policy created with PingAccess as Type.

- Click Save.
Notes:
- If you intend to use TLS version strings, the following must be separated by a comma, as shown below:
agent.ssl.protocols=TLSv1.1, TLSv1.2 - TLSv1.3 is currently not supported for PingAccessAgent.
