Application Rules
Overview
This guide explains the application specific rules for WAF.
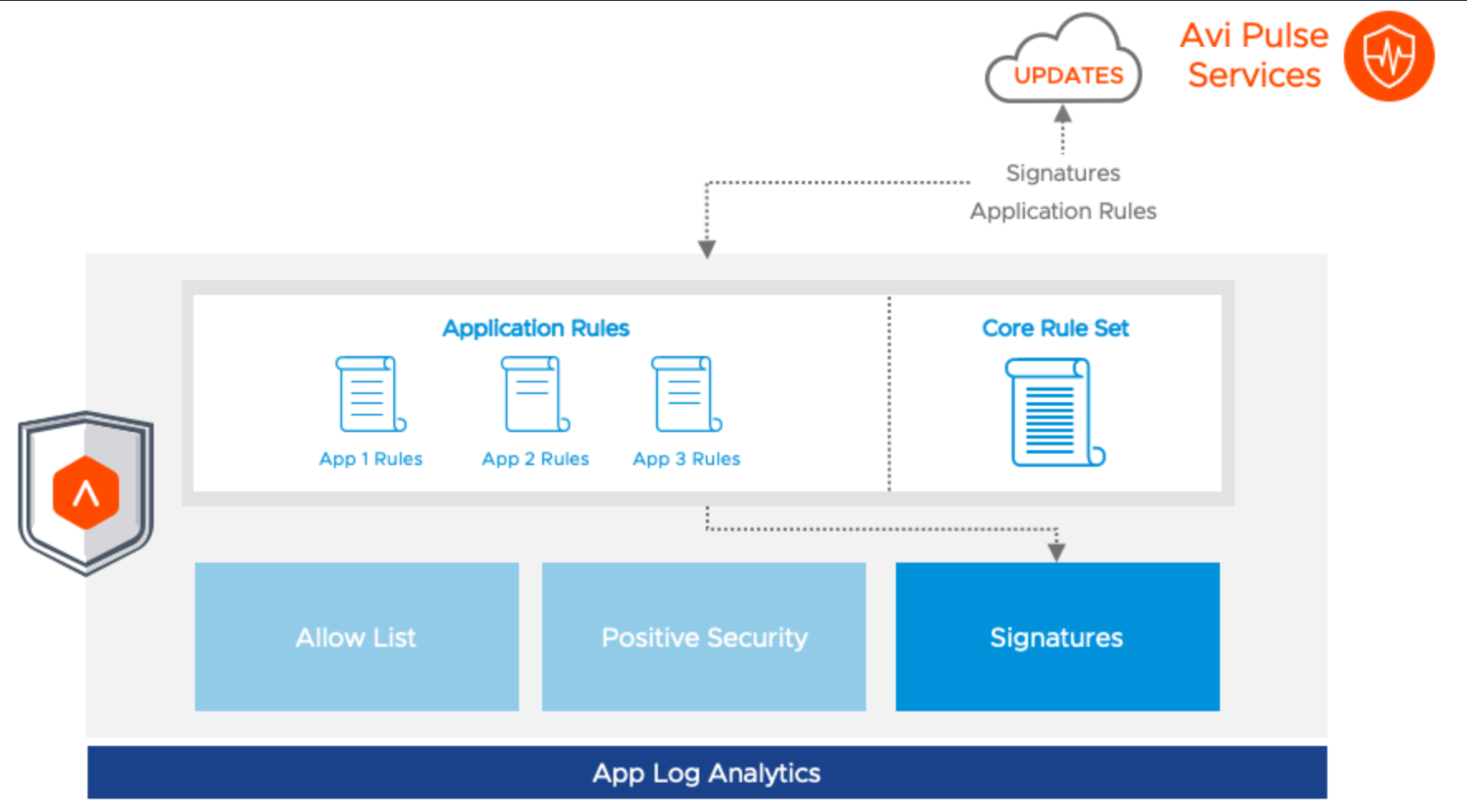
To secure applications with known vulnerabilities starting from version 20.1.5 the WAF supports the use of Application Rules.
These Application Rules are specifically designed to block attacks on known application vulnerabilities (many of them with CVEs). They are automatically updated using the Application Rules of the Avi Pulse service.
When the admin enables this protection, more than 5000 applications can be selected, thereby activating the specific application rules for that application in the WAF Policy guide.
Configuring Application Rules
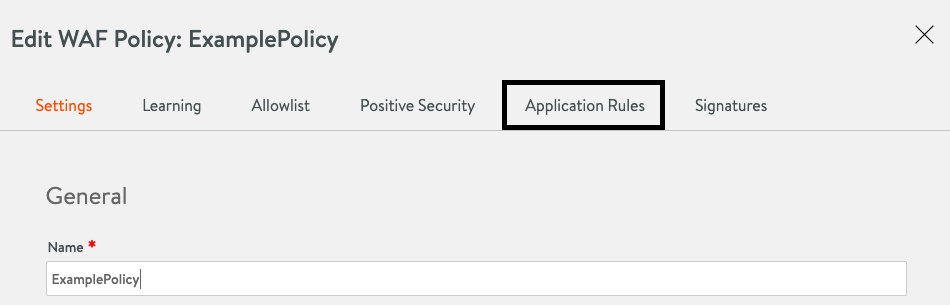
To configure Application Rules, you need to select a new entry in the WAF Policy tab.
After selecting this tab, you can choose the Application Rules using the Add search bar.
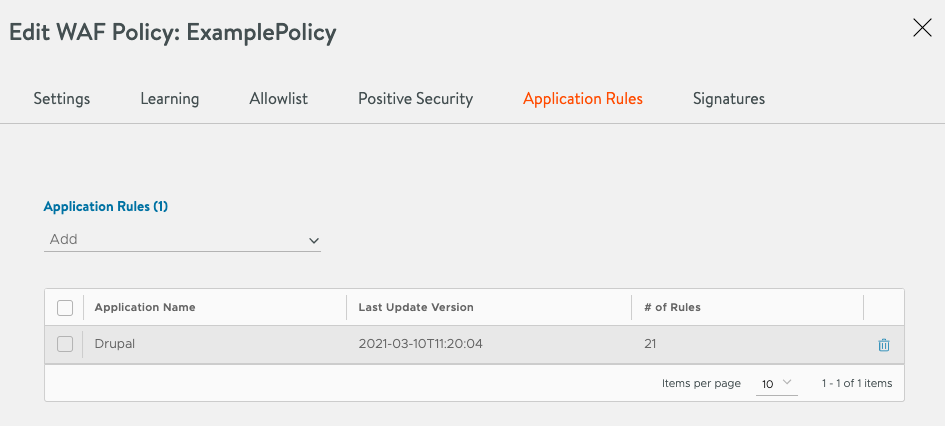
When an application is selected, it is added to the list of currently configured applications and will showcase the application name, the last update timestamp, and the number of rules for this application.
Example:
In this example, Drupal has been chosen as the Application to protect. The policy now contains 21 rules that are active and protect against specific exploits known for Drupal.
To remove an application from the list, use the trashcan button in its row.
Updating Application Rules
You need to register to the Application Rules of the Avi Controller using Application Rules for Pulse guide, else the Application Rules feature will not work.
Application Rules are then updated daily automatically.
Updates are applied to any WAF policy with a configured application.
Note: If a rule has been disabled, this change will be kept when an update is applied.
App Log Analytics
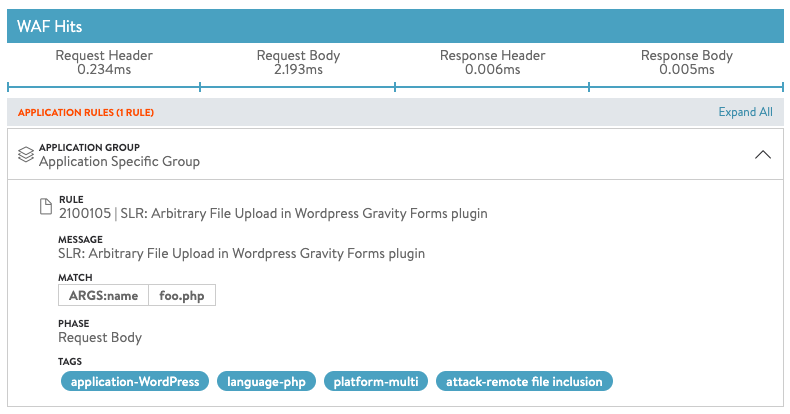
When an Application Rule is hit, the App Log Analytics captures the event.
It contains all information about the type of attack that it has detected. It is seamlessly integrated with all other parts of the WAF functionality.
Tuning of Application Rules
The nature of the specific protection provided by Application Rules makes it easy to deploy. False positives are not existent because the signatures are targeting only specific attack vectors.
Note that in contrast to the
In case there is a need to tune a rule, it can be disabled using the following CLI:
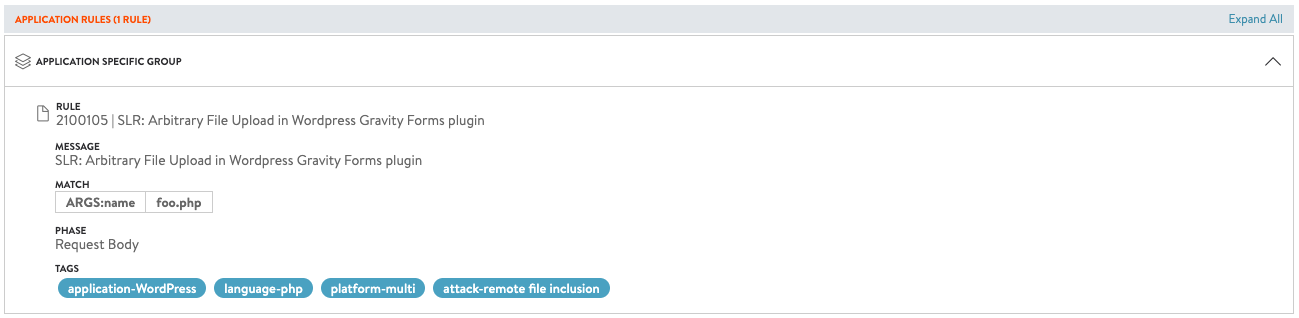
Note: The rule ID in the above CLI is 2100105.
Steps to Configure via CLI
You can disable rule using the rule ID 2100105 as follows:
ssh to Controller
shell (login)
configure wafpolicy System-WAF-Policy
application_signatures
where
CTRL/F or CMND/F for rule ID: 2100105 -> note index
rules index 14160
no enable
save
save
save
The rule is now disabled.
| rules[500] | |
| index | 14160 |
| name | SLR: Arbitrary File Upload in Wordpress Gravity Forms plugin |
| rule_id | 2100105 |
| enable | False |
| rule | <sensitive> |
| tags[1] | application-WordPress |
| tags[2] | language-php |
| tags[3] | platform-multi |
| tags[4] | attack-remote file inclusion |
| is_sensitive | True
Troubleshooting
-
Application Rules template is empty
-
Check if the Controller is registered with Avi Pulse
-
Check if Download Application Rules opt-in is set
-
Check config audit log for ALBSERVICES entries
-
-
Application Rules block a Legitimate Request
- Check disabling an Application Rule in Steps to Configure via CLI section above
-
Application Rules are not getting updated
-
Check ALBSERVICES config audit log for details
-
Update interval is daily. Update check can be done more often. You can check again the next day.
For more details on Pulse connection, refer to Getting Started with Avi Pulse guide.
-
-
My application is not listed in Application Rules
The system will display We are sorry to hear that. If you think the application, you are protecting should be included, please open a support case to ask for inclusion. Include any CVE that is relevant for the request. message.
Note: Exclusions are not available for Application Rules. The main reasons is, that these rules are specific and usually only match to a specific parameter on a specific URL. Excluding this parameter from the rule is the same as disabling the rule.
Document Revision History
| Date | Change Summary |
|---|---|
| April 15, 2021 | Published Application Rules for WAF Guide |