Web App Security
Protect Applications with Context-Aware Security
Web Application and API Protection (WAAP) with Real-Time App Security Insights
VMware NSX Advanced Load Balancer delivers multi-cloud security to protect applications and microservices from today’s threats and improve ingress control. NSX ALB’s comprehensive solution provides network and application security with a context-aware web application firewall (WAF) to protect against all forms of digital threats. Visibility through advanced analytics and security insights helps customize a comprehensive application security policy per application, microservice, or tenant.
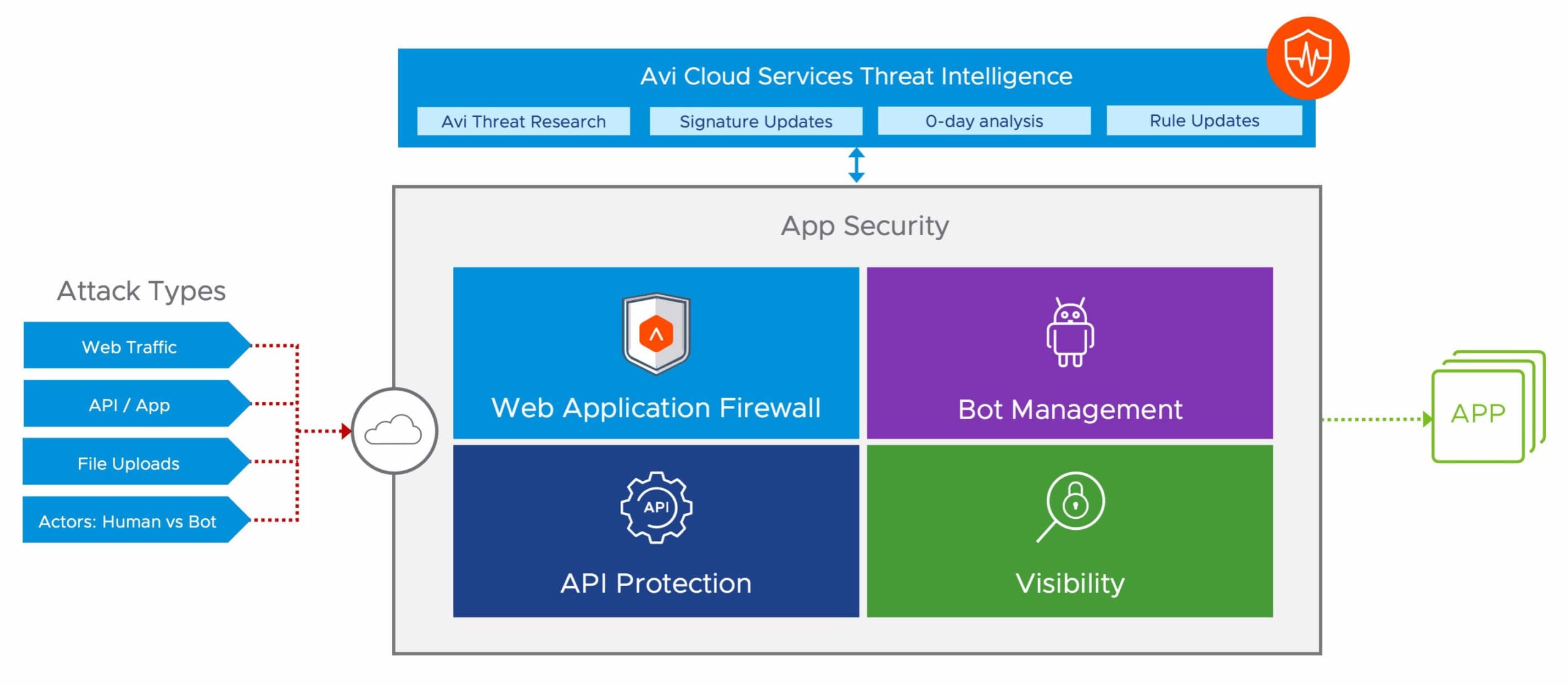
NSX ALB WAF offers ingress security through a comprehensive set of web app security features to protect applications and APIs. It helps achieve compliance with GDPR, HIPAA and PCI DSS security standards. NSX ALB minimizes false positives with a positive security model, WAF learning mode and advanced application security analytics. It protects applications from DDoS attacks, malicious bots and OWASP top 10 threats with real-time app security insights and visibility.
Security and WAF is delivered as part of the NSX ALB Platform which provides a distributed web security fabric with central policy management, on-demand autoscaling, and built-in analytics for securing multi-cloud applications.
I believe there is no valid reason to provision a web application on the internet without a WAF. This is especially important to us since Swisslos needs to be compliant with industry regulations and certifications.
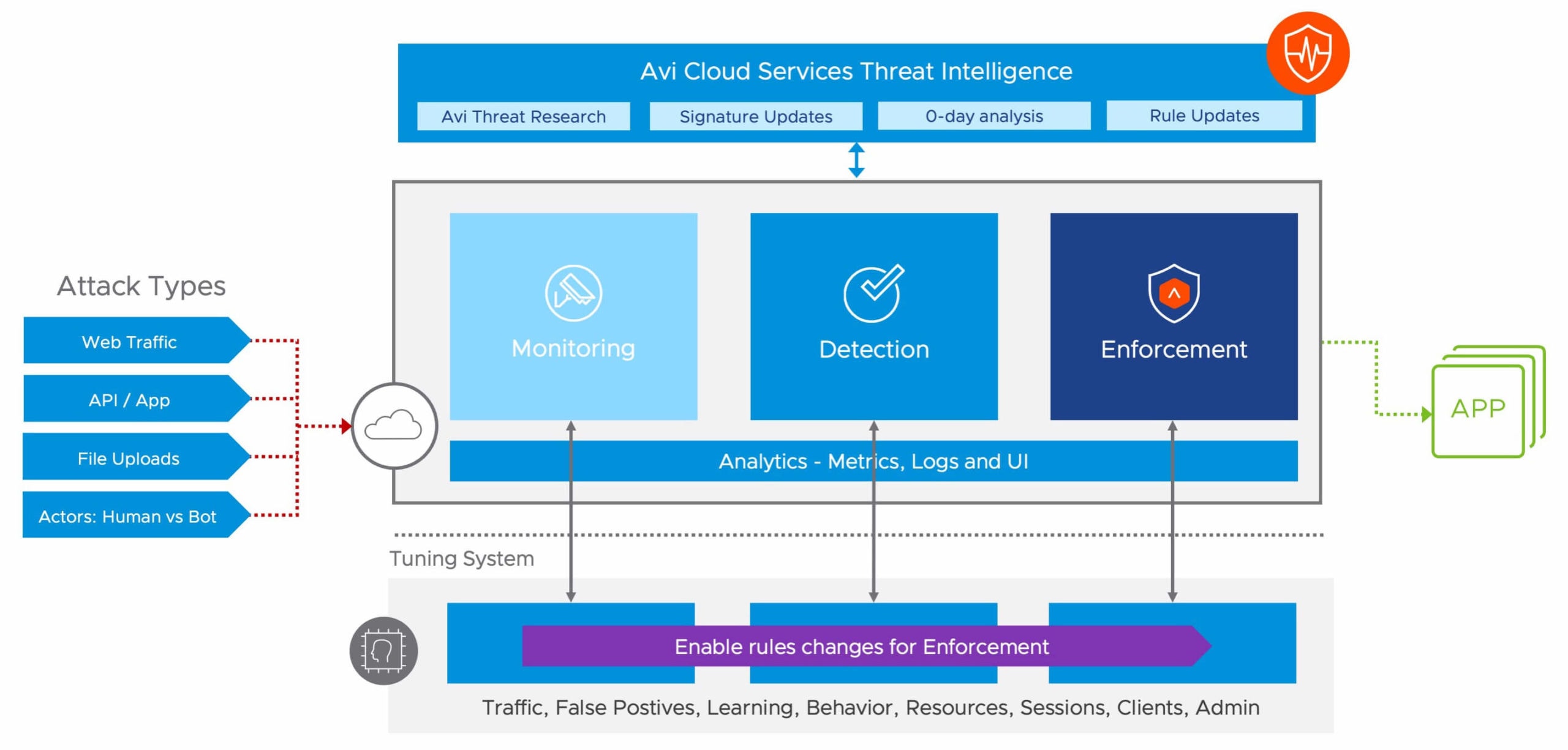
Optimized Web App Security Pipeline
- Application allow-list effectively bypasses known, trusted sources such as DAST scan output and internal IP addresses
- Positive security with WAF learning mode efficiently models good traffic behavior with automatically programmed rules
- Signature-based protection is based on core rule set (CRS), live feeds from Avi Cloud services and application-specific frameworks
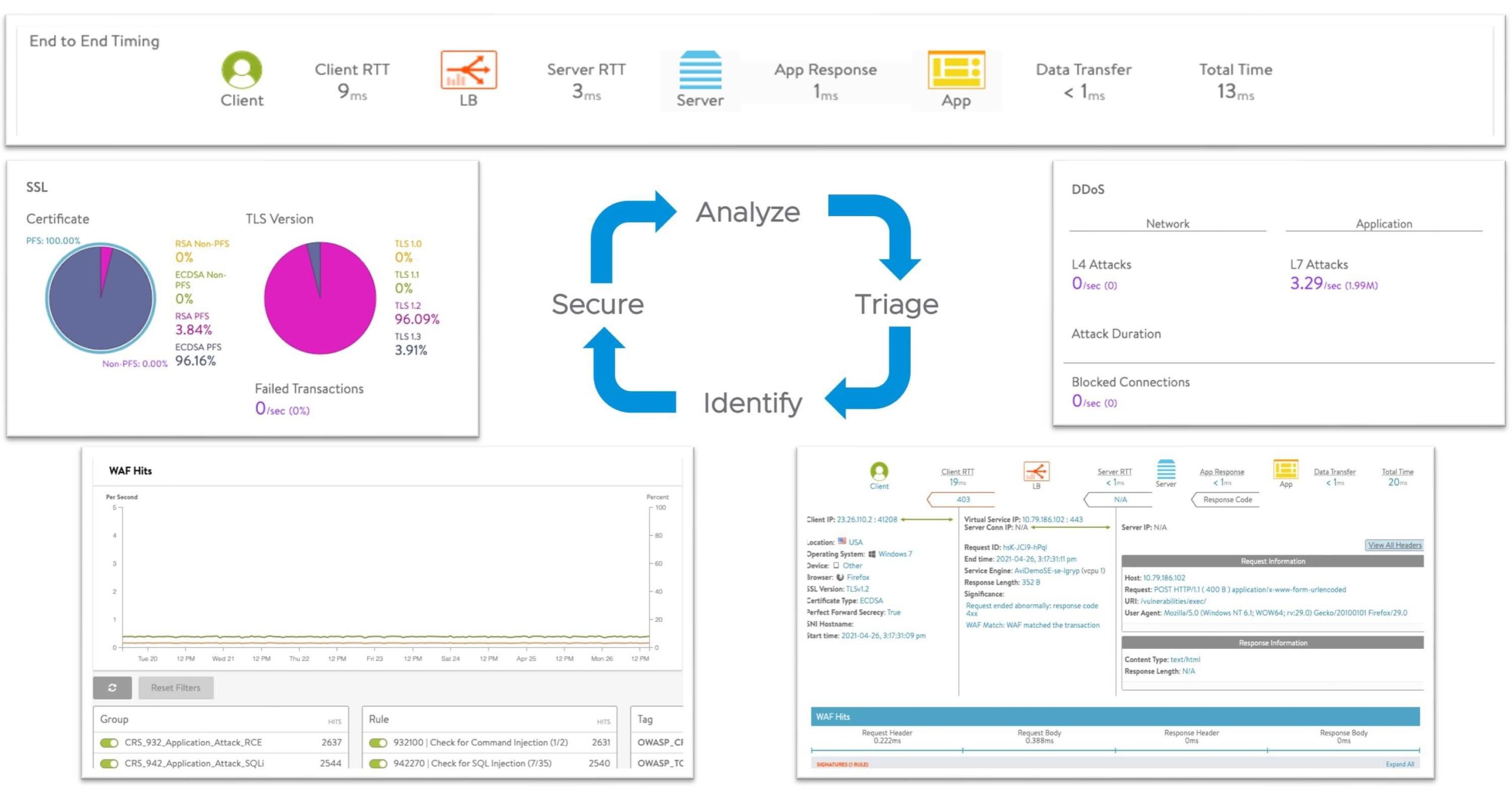
Real-Time App Security Insights
- Real-time visibility and application security analytics includes SSL versions, ciphers, real-time DDoS attack data, and system health scores
- Granular app security insights on traffic flows and rule matches help inform precise policies
- One-click customization of rules and exceptions significantly reduces the problem of false-positives
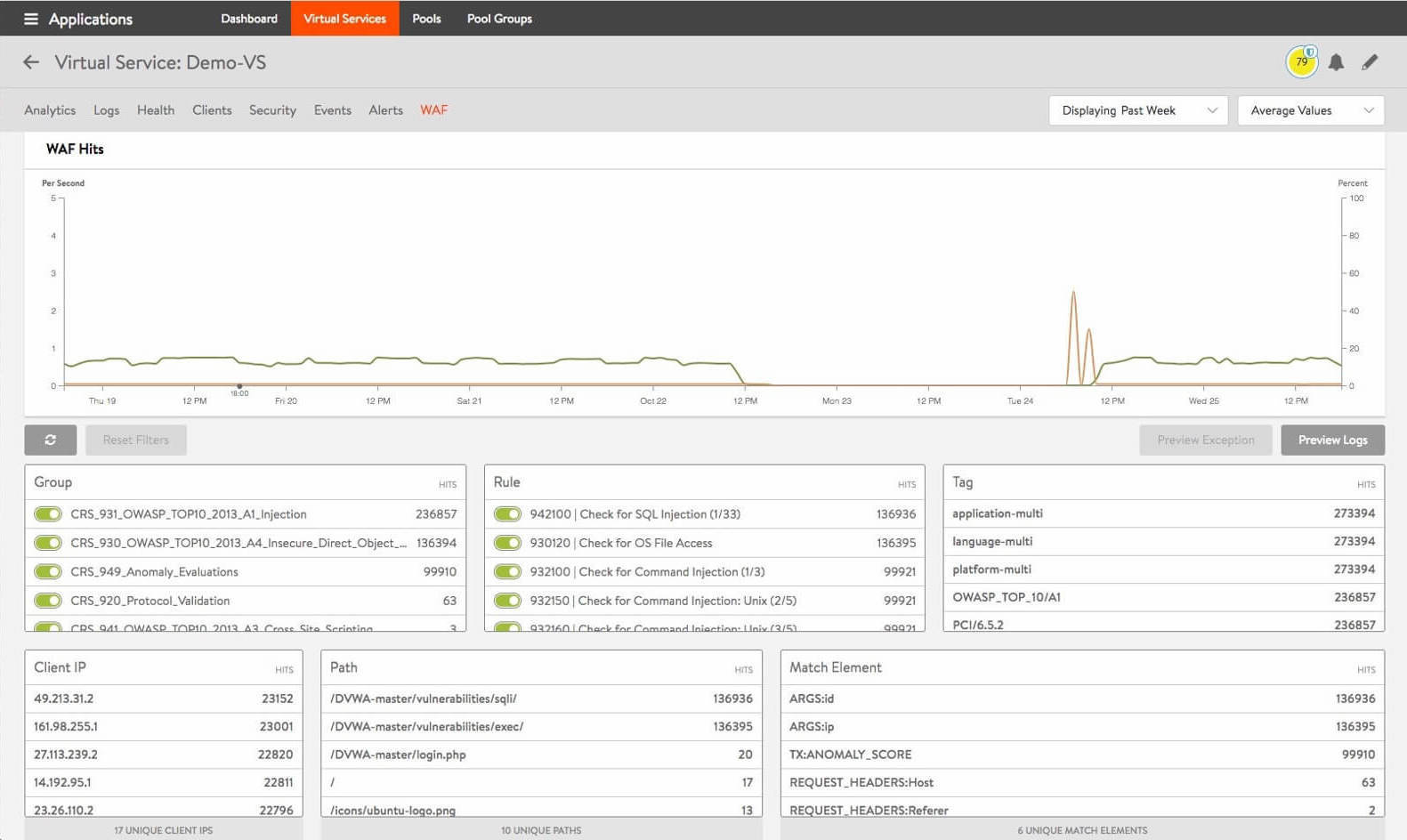
Centralized Application Security Management
- OWASP Top 10 threats including Input protection (SQL injection, cross-site scripting (XSS), local/remote file inclusion, remote code execution, PHP code injection, path traversal, session fixation)
- HTTP validation (limit HTTP allow method, encoding bypass detection, HTTP response splitting, HTTP parameter pollution)
- Malicious bot protection
- Data leakage protection (error message suppression, leakage of personally identifiable information such as credit card or SSN numbers)
- Network attack protection (SYN Flood, Network DDoS)
Context-Aware Application and API Protection Made Simple
- A comprehensive application security stack includes WAF, application rate limiting, DDoS protection, SSL/TLS encryption, bot mitigation, access control list (ACL), authentication and authorization, and L3-L7 security rules.
- Support for application and microservices environments
- Per-app deployments and elastic auto scaling across data centers and multi-cloud environments
- GDPR, HIPAA, and PCI compliance with a scalable and distributed application security platform
- A distributed web app security fabric uses built-in analytics to make intelligent decisions

