Reverse Proxy Server Definition
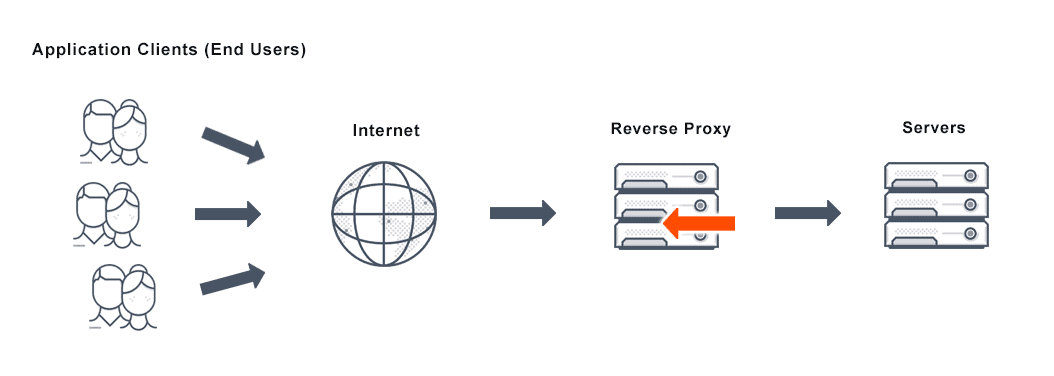
A Reverse Proxy Server, sometimes also called a reverse proxy web server, often a feature of a load balancing solution, stands between web servers and users, similar to a forward proxy. However, unlike the forward proxy which sits in front of users, guarding their privacy, the reverse proxy sits in front of web servers, and intercepts requests. In other words, a reverse proxy acts on behalf of the server, while a proxy acts for the client.
Frequently, popular web servers protect the application frameworks of more limited HTTP capabilities using reverse-proxying functionality. Relevant weaknesses in this context include limitations in handling the complete range of request formats that can adhere to HTTP(S) 1.x, HTTP(S) 2.x, or difficult to detect requests, and limited ability to handle excessive loads. In these situations, a reverse proxy server could use the shielded server load as a basis for buffering incoming requests, transform one request into multiple requests to synthesize responses, handle data from cookies or sessions, or create HTTP requests from HTTPS requests, for example.
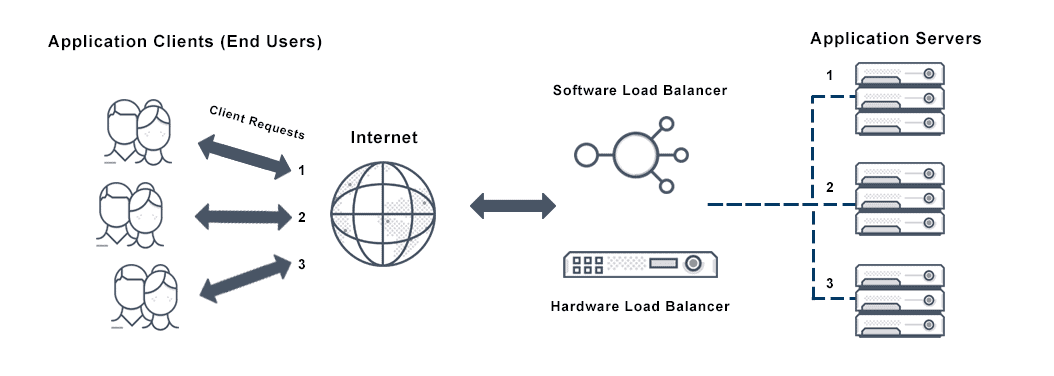
A reverse proxy server acts like a middleman, communicating with the users so the users never interact directly with the origin servers. It also balances client requests based on location and demand, and offers additional security.
Here are a few frequently asked questions about reverse proxy servers:
Reverse Proxy Server vs Proxy Server
The simple difference between a forward proxy server and a reverse proxy server is a forward proxy sits in front of users. It stops origin servers from directly communicating with that user.
What Does a Reverse Proxy Server Do?
A reverse proxy ultimately forwards user/web browser requests to web servers. However, the reverse proxy server protects the web server’s identity. This type of proxy server also moves requests strategically on behalf of web servers, typically to help increase performance, security, and reliability.
Reverse Proxy Servers can:
- Disguise the characteristics and existence of origin servers.
- Make initiating takedowns and removing malware easier.
- Carry TLS acceleration hardware, enabling them to perform TLS encryption in place of secure websites.
- Distribute load from incoming requests to each of several servers that supports its own application area.
- Function as web acceleration servers, caching dynamic content and static content, reducing load on origin servers.
- Compress content, optimizing it and speeding loading times.
- Perform multivariate testing and A/B testing without inserting JavaScript into pages.
- Add basic HTTP access authentication to web servers that lack authentication.
- “Spoon-feed” dynamically generated pages bit by bit to clients even when they are produced at once, allowing the pages and the program that generates them to be closed, releasing server resources during the transfer time.
- Analyze many incoming requests via a single public IP address, delivering them to multiple web-servers within the local area network.
What are some Common Uses for Reverse Proxy Servers?
A common reverse proxy server example happens when a company has a large e-commerce website. It can’t handle its incoming traffic with just one server, so it uses a reverse proxy server to direct requests from its users to an available server within the pool. There are various methods to direct this traffic, such as round robin load balancing.
Another great use for a reverse proxy server is to cloak a site’s main server because they are concerned about protecting the server from malicious attacks by users. Such a site can appear to be hosted among many servers, and typically only public-facing servers do go down, protecting the backend server.
What are the Benefits of a Reverse Proxy Server?
Benefits of reverse proxy servers include:
- load balancing
- global server load balancing (GSLB)
- caching content and web acceleration for improved performance
- more efficient and secure SSL encryption, and
- protection from DDoS attacks and related security issues.
For many sites, but especially for high-volume websites, a single origin server will not be sufficient to handle all inbound site traffic. A reverse proxy server can handle numerous requests for the same site, distributing them to different servers in an available pool.
This more evenly distributes inbound traffic, or balances the load among multiple servers, so no one web server will become overloaded. Should a single server completely fail, the reverse proxy server can redirect the other servers to manage the traffic.
Global Server Load Balancing (GSLB) is load balancing distributed around the world by a reverse proxy. With this kind of load balancing, requests to a website can be distributed locally. This shortens the distances and times that requests and responses need to travel, in turn reducing load times.
Similarly, a reverse proxy cache server can enhance performance by caching local content. This kind of caching improves speed and user experience, especially for sites that feature dynamic content.
Businesses can also save money using a reverse proxy server to encrypt all outgoing responses and decrypt all incoming requests. By handling all communications this way via reverse proxy, the company avoids the much higher cost of encrypting and decrypting SSL communications between clients and servers on the main production server.
Likewise, a reverse proxy server offers protection from attacks. This is because no service or site need ever reveal its web server’s IP address with a reverse proxy in place, and because reverse proxies offer a traffic scrubbing effect.
Protecting the server’s IP address means attackers can only target the reverse proxy, rendering DDoS and related attacks much more difficult. A reverse proxy server also scrubs all incoming traffic, distributing all requests from the internet among a secure group of servers during a DDoS attack to mitigate against its overall impact.
Reverse proxies are well-suited to battling cyber attacks, capable of hosting web application firewalls and other tools for shutting out malware such as hacker requests and bad bots.
Is There a List of Reverse Proxy Servers?
Common reverse proxy servers include hardware load balancers, open source reverse proxies, and reverse proxy software. Reverse proxies are offered by many vendors such as VMware, F5 Networks, Citrix Systems, A10 Networks, Radware, and Public Cloud platforms such as Amazon Web Services and Microsoft Azure.
How to Setup a Reverse Proxy Server?
Enterprises spend several weeks planning, procuring, and deploying specialized hardware to setup reverse proxy servers. These solutions can be expensive and require complex operational steps from IT teams.. However, modern applications and multi-cloud environments can benefit from advanced software-defined reverse proxy servers which simplify operations with distributed multi-cloud architectures at lower costs.
Does Avi Provide a Reverse Proxy Server?
VMware NSX Advanced Load Balancer is architected as a reverse proxy server and it is just one part of the cloud-native, elastic load balancing solution that it delivers. The Avi platform also delivers reverse proxy server security capabilities with web application firewall and DDoS mitigation.
With the Avi Platform your business achieves a quick, secure, scalable application experience. Avi stands apart from legacy load balancers as the 100 percent software-defined option. It provides:
- Multi-cloud – an orchestrated, consistent experience across cloud and on-premises environments through central management
- Intelligence – Avi’s baked-in analytics provide actionable insights that render automation intelligent, autoscaling seamless, and decisions simpler
- Automation – application delivery integrated into the CI/CD pipeline and self-service provisioning, thanks to 100% RESTful APIs
For more on the actual implementation of load balancers, check out our Application Delivery How-To Videos.
In addition to a Software Load Balancer, the multi-cloud application services also include Web App Security and Container Ingress.