Private Cloud Architecture Definition
Private cloud architecture pools resources in a data center in a single logical structure. Virtual machines and containerized hardware and software components enable organizations to better utilize their private cloud infrastructure and increase their efficiency.
Private Cloud Architecture FAQs
What is Private Cloud Architecture?
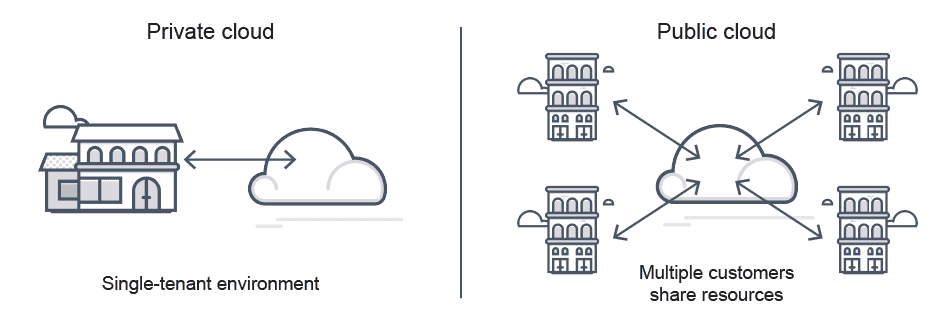
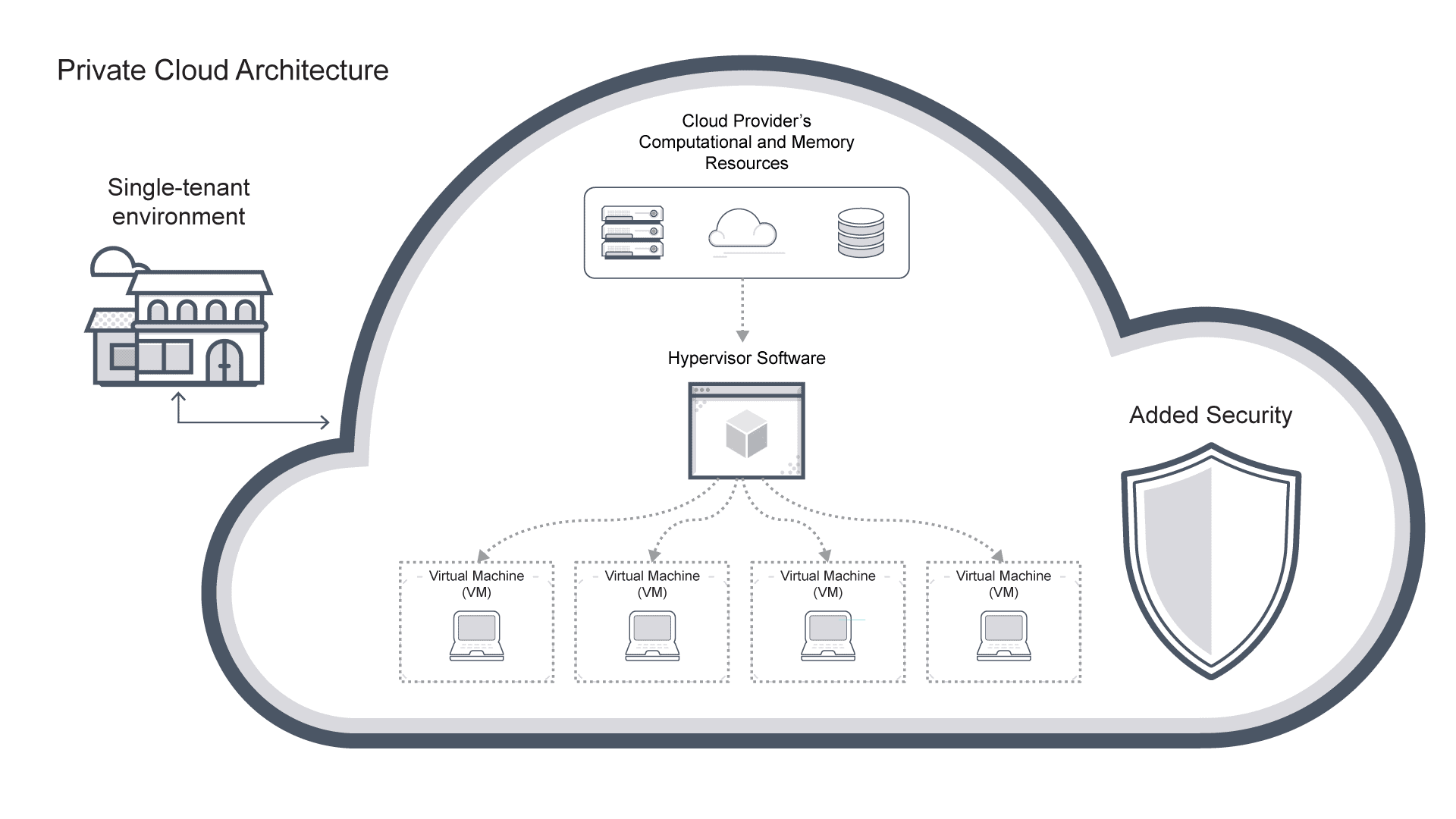
What is a private cloud architecture? Private cloud architecture is a single tenant environment dedicated to computing for one organization or entity. It is designed to offer similar benefits as public cloud services, such as scalability, flexibility, and self-service capabilities, but with added control and security.
In a private cloud infrastructure architecture, all underlying servers, storage, and networking resources, exclusively serve the organization. Either the organization or a third-party service provider also owns and manages all underlying infrastructure.
This contrasts with public cloud services, where the infrastructure is shared among multiple users and is always managed by the cloud service provider.
How Does a Private Cloud Architecture Work?
Private cloud database architecture typically involves virtualization technologies such as hypervisors. These enable users to create virtual machines (VMs) or containers atop physical hardware. Administrators can manage and provision virtualized resources dynamically, accommodating rapid, on-demand scalability and resource allocation.
Organizations can deploy private clouds on-premises within their own data centers or off-premises in a dedicated facility managed by a service provider. Organizations can also deploy private clouds using a hybrid cloud strategy—a combination of on-premises and off-premises resources.
Key characteristics of private cloud architecture include:
Single-tenancy. The cloud infrastructure is dedicated to a single organization, ensuring data isolation and enhanced security.
Control and customization. The organization has greater control over the infrastructure, allowing for tailored configurations, security policies, and compliance measures.
Resource pooling and self-service. Virtualized resources are pooled together, enabling self-service provisioning for users within the organization. This means users can request and deploy computing resources on-demand without requiring manual intervention from IT staff.
Scalability and elasticity. The private cloud works to scale and respond based on demand, so organizations can allocate resources efficiently and cost-effectively.
Enhanced security and privacy. Private clouds provide a higher level of security since they are isolated from other organizations. This can be particularly important for industries with strict regulatory requirements or sensitive data.
Benefits of Private Cloud Network Architecture
Private cloud security architecture offers several benefits for organizations. Here are some of the key advantages:
Enhanced control and security. Private clouds offer greater security compared to public clouds. Dedicated infrastructure minimizes the risk of data breaches and unauthorized access. It also allows organizations to implement custom security measures, firewalls, encryption, and access controls for sensitive data and regulatory requirements. A private cloud enables customized configurations, security policies, and network settings, which is especially valuable for industries with strict compliance needs or unique IT environments.
Improved performance. Since the resources of private clouds are exclusive to one organizational user, they deliver better performance and reduced latency. Dedicated infrastructure ensures consistent, predictable performance suitable for applications with high computational or network demands.
Customized, tailored solutions. Private cloud architecture enables organizations to design and deploy tailored, cost-efficient solutions. They can choose the hardware, storage, and networking components that best suit their workload needs and optimize performance.
Scalability and flexibility. Private clouds are elastic, allowing organizations to scale resources on demand. This flexibility enables efficient resource allocation, ensuring that computing power and storage are available as needed without overprovisioning or underutilization.
Compliance and data sovereignty. Industries such as healthcare, finance, and government have strict compliance and data sovereignty regulations. Private clouds enable organizations to maintain compliance with industry-specific regulations and ensure data sovereignty without relying on external cloud service providers.
Greater reliability. Organizations have dedicated resources and can implement redundancy measures, such as backup and disaster recovery solutions, tailored to their needs. This minimizes the risk of downtime and data loss for private clouds.
Cost optimization. While private clouds require upfront investment in infrastructure, they can offer long-term cost savings, especially for organizations with predictable workloads or a need for a high degree of compliance or control over infrastructure.
Use Cases for Private Cloud Environments
Here are some common use cases for private cloud environments:
Government agencies. Government agencies often deal with sensitive data and have strict compliance and data sovereignty requirements. Private cloud architectures enable them to maintain control over their infrastructure and data while meeting regulatory standards.
Healthcare organizations. Healthcare providers handle vast amounts of sensitive data such as patient information, and private clouds offer the security and control necessary to ensure compliance with healthcare regulations, such as the Health Insurance Portability and Accountability Act (HIPAA).
Financial institutions. Banks, insurance companies, and financial organizations handle critical financial data and must meet stringent regulatory requirements; private clouds help them meet compliance standards while controlling their data and IT infrastructure.
Educational and research institutions. Academic institutions and research organizations demand large-scale computational resources, data storage capabilities, e-learning platforms, and security for sensitive student data for compliance with regulations such as HIPAA and the Family Educational Rights and Privacy Act of 1974 (FERPA).
Manufacturing and industrial sector. Manufacturing companies often have unique IT needs, such as resource-intensive applications or large-scale IoT (Internet of Things) deployments. Private clouds offer dedicated infrastructure for managing production systems, controlling data flow, and optimizing manufacturing processes.
These are just a few examples of many possible applications for private cloud architectures.
Designing Private and Hybrid Cloud Architecture: Best Practices
Designing and building a private cloud architecture involves careful planning and consideration of various factors. Here are some best practices and private cloud architecture principles to consider:
Define clear objectives. Clearly define the specific organizational objectives and requirements, such as scalability, security, compliance, and performance. This should guide the design process and inform decisions.
Assess workload requirements. Evaluate workload requirements, including computing power, storage, and networking. Identify the characteristics of each workload, such as resource usage, performance needs, data sensitivity, and interdependencies. This assessment will help determine the infrastructure and resources required for a private or hybrid cloud architecture.
Plan for scalability and elasticity. Design the architecture to accommodate future growth and changing demands. Incorporate scalability and elasticity features to ensure that resources can be easily added or removed as needed. This flexibility will optimize resource utilization and cost-efficiency.
Consider data management. Data management is crucial for both private and hybrid clouds. Determine how the system and users will store, protect, and access data. Implement appropriate backup and disaster recovery mechanisms to ensure data availability and integrity. Consider data classification and encryption to meet security and compliance requirements.
Security and compliance. Emphasize security and compliance. Implement robust security measures such as access controls, encryption, firewalls, and intrusion detection systems. Consider industry-specific compliance requirements such as HIPAA, GDPR, or PCI DSS. Regularly update and patch infrastructure to address security vulnerabilities.
Automation and orchestration. Streamline provisioning, deployment, and resource management with automation and orchestration tools. Implement monitoring and management tools to track performance, usage, and security. This enables self-service, reduces manual effort, and ensures consistent resource configuration.
Network design and connectivity. Careful network design can ensure optimal connectivity and performance. Plan for redundancy, load balancing, and fault tolerance. Consider network segmentation to isolate sensitive workloads and implement appropriate network security controls.
Testing and evaluation. Test cloud architecture regularly to identify performance, security, or scalability issues. Conduct load testing, vulnerability assessments, and disaster recovery drills. Continuously evaluate architecture and optimize its performance to meet evolving requirements.
Collaboration and documentation. Document architecture design, configurations, and operational procedures to foster successful collaboration and facilitate knowledge transfer among different teams, including IT, security, operations, and compliance.
Plan for integration if needed. If designing a hybrid cloud architecture, plan for integration between private and public cloud environments. Ensure seamless connectivity, data transfer, and identity management, and implement hybrid cloud management tools.
Types of Cloud Computing Architectures
Having discussed what private cloud computing architecture is and how it works, how does it compare to other types of cloud computing architectures?
Virtual Private Cloud Architecture
The Virtual Private Cloud (VPC) architecture cloud computing model combines the benefits of both private and public clouds. VPC provides a logically isolated and customizable virtual network within a public cloud infrastructure.
A standard private cloud architecture allows an organization to own and manage its own dedicated physical infrastructure, including servers, storage, and networking equipment. It offers complete control over the infrastructure and allows for customization and security measures tailored to the organization’s needs. A standard private cloud can be deployed on-premises or in a dedicated off-premises facility.
In contrast, a virtual private cloud (VPC) architecture is built within a public cloud provider’s infrastructure, such as Amazon Web Services (AWS) or Google Cloud Platform (GCP). It still offers some of the characteristics of a private cloud, such as isolation, control, and security, but does not require users to manage physical infrastructure.
Here are some key differences and advantages of virtual private cloud architecture compared to standard private cloud architecture:
Ownership. In private cloud architecture, the organization owns and manages the physical infrastructure, while in a VPC architecture, a public cloud provider owns and manages the infrastructure, and the organization only has control over the virtual networking components within that infrastructure.
Elasticity and scalability. Since VPC architecture leverages the scalability and elasticity features of a public cloud provider, allowing organizations to scale resources up or down based on demand, it may offer more readily available dynamic scalability compared to standard private clouds which are self-limited as a resource.
Rapid provisioning. Virtual private cloud architectures enable rapid provisioning and configuration of resources such as virtual networks, subnets, and security groups by using underlying infrastructures that are already in place.
Global availability. Public cloud providers typically offer global availability and multiple data center regions, and with that, geographical redundancy, low latency, and improved performance around the world.
Integration with public cloud services. Virtual private cloud architectures can integrate with other public cloud services from the same cloud provider, enabling organizations to use AI/ML, analytics, databases, serverless computing, storage, and other services within the VPC environment.
Pay-as-you-go model. VPC architectures follow the public cloud pay-as-you-go pricing model so organizations pay for the resources they use, which can be more cost-effective compared to private cloud infrastructure.
Security and compliance. Virtual private cloud architectures provide strong security and isolation via access control mechanisms, virtual network segmentation, and security groups.
Managed Private Clouds
Managed private clouds are fully managed private cloud environments. That third-party service provider manages the infrastructure setup, maintenance, security, and monitoring. This offers the benefits of a private cloud while offloading the management burden of managing the underlying infrastructure to an expert service provider.
Hosted Private Clouds
Hosted private clouds are private cloud environments where the physical infrastructure is owned and operated by a third-party service provider who builds and maintains infrastructure in their data centers and offers it as a service. This frees organizations from needing their own data center infrastructure, but allows them to keep control over their own virtual infrastructure.
Managed Private Clouds vs Hosted Private Clouds—What’s the Difference?
The key difference between hosted private clouds and managed private clouds is the level of responsibility and control. The organization with a hosted private cloud retains control over the virtual infrastructure, but leaves management of the underlying physical infrastructure to the service provider or host. In a managed private cloud, the service provider takes care of both the physical and virtual infrastructure, providing a fully managed cloud environment for the organization, which handles neither set of tasks.
Infrastructure as a Service (IaaS)
IaaS is a cloud computing model where organizations can provision and manage virtualized computing resources, such as virtual machines, storage, and networking, on-demand. It offers flexibility and scalability by providing infrastructure resources as a service. IaaS can be delivered in public, private, or hybrid cloud environments. In the context of private clouds, organizations can build their own IaaS environment within their private cloud architecture, enabling self-service provisioning and management of infrastructure resources.
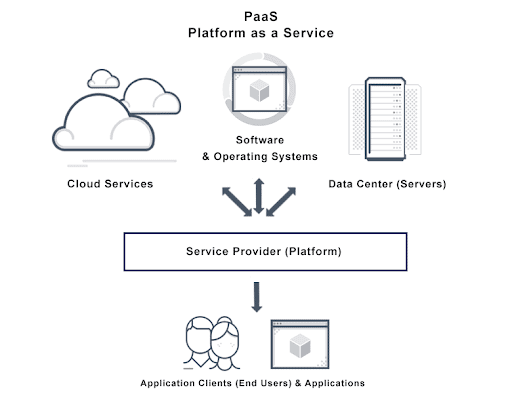
Platform as a Service (PaaS)
PaaS is a cloud computing model where a provider offers a platform and development environment as a service. It allows organizations to develop applications and manage them without any need to support the underlying infrastructure. PaaS provides a pre-configured computing platform with frameworks, libraries, and other tools, freeing engineers to work on development and deployment. While PaaS can be built on top of private cloud infrastructure, it is not limited to private clouds and can be offered in public or hybrid cloud environments as well.
Infrastructure as a Service (IaaS) vs Platform as a Service (PaaS)—What’s the Difference?
IaaS provides the fundamental building blocks of computing infrastructure in the cloud. PaaS takes the abstraction level a step further by providing a complete platform for developing, deploying, and managing applications.
The difference between them is abstraction and application. IaaS provides virtualized infrastructure resources such as servers, storage, and networking that organizations manage, while PaaS goes a step further by providing a complete application development and deployment platform, abstracting away the underlying infrastructure complexity.
Multi-tenant Architecture in a Private Cloud
Multi-tenant architecture is an approach that shares a single instance of a software application or infrastructure between multiple tenants or organizations. Implementing multi-tenancy in the context of private cloud infrastructure allows multiple departments or business units within an organization to share resources while maintaining isolation and security, enabling efficient resource utilization and cost-sharing.
Private Cloud vs Public Cloud vs Hybrid Cloud Architecture—What’s the Difference?
Private cloud architecture is typically hosted on-premises or in a dedicated off-premises data center and is dedicated to a single organization. It offers exclusive access and control over the infrastructure, allowing organizations to customize the environment according to their specific needs.
Private cloud vs public cloud infrastructures provide enhanced security, compliance, and customization options, making this approach suitable for organizations with strict data privacy requirements or specialized IT environments. They can be managed by the organization itself or outsourced to a managed service provider.
Public cloud architectures are cloud services provided by third-party vendors over the internet. Resources such as computing power, storage, and applications are shared among multiple organizations or tenants.
Public cloud providers own and manage the infrastructure, providing scalability, elasticity, and a wide range of services based on a pay-as-you-go model. Public clouds are cost-effective, require no upfront investment, and offer global availability, but they may have limited customization options and are subject to the provider’s security measures and compliance certifications.
Hybrid cloud architectures combine private and public clouds, allowing organizations to make use of resources across private and public cloud environments. Hybrid clouds provide flexibility, allowing organizations to optimize resource allocation, scale workloads, and take advantage of cost-effective public cloud services when needed.
For example, organizations may use the private cloud for sensitive workloads, data, and applications that require high security or compliance, while utilizing the public cloud for scalable, on-demand resources and services. However, managing integration, data transfer, and security between the two environments can be complex.
Examples of Private Cloud Architecture
There are several private cloud architecture solutions available on the market, offered by various vendors. Here are some examples of well-known private cloud solutions:
VMware Private Cloud Architecture. VMware vSphere is a virtualization platform that enables organizations to create and manage private cloud environments. It offers a suite of virtualization technologies for compute, storage, and networking, along with management tools for resource provisioning, monitoring, and automation.
Azure Private Cloud Architecture. Azure Stack is Microsoft’s hybrid cloud solution that allows organizations to extend Azure services to private data centers. It enables organizations to build and manage private clouds using Azure-consistent services and APIs, providing a consistent development and management experience across public and private cloud environments.
OpenStack Private Cloud Architecture. OpenStack is an open-source cloud computing platform that allows organizations to build and manage private clouds using a comprehensive set of services, including compute, storage, networking, and identity management.
Amazon Private Cloud Architecture. Amazon Web Services (AWS) offers the private cloud architecture solution Amazon Virtual Private Cloud (Amazon VPC) that enables organizations to create a logically isolated virtual network within the AWS cloud.
Does Avi Offer a Private Cloud Architecture Solution?
Avi’s application delivery controller (ADC) solution is designed to improve the performance, security, and availability of applications in a range of environments. Avi’s ADC provides load balancing, traffic management, SSL/TLS termination, application security, and other services, enhancing application delivery in on-premises data centers and across cloud environments. Learn more about Avi’s multi-cloud load balancing capabilities and more here.