Web Application Firewall Definition
A Web Application Firewall or WAF provides web application security for online services from malicious Internet traffic. WAFs detect and filter out threats such as OWASP Top 10 which could degrade, compromise or bring down online applications.
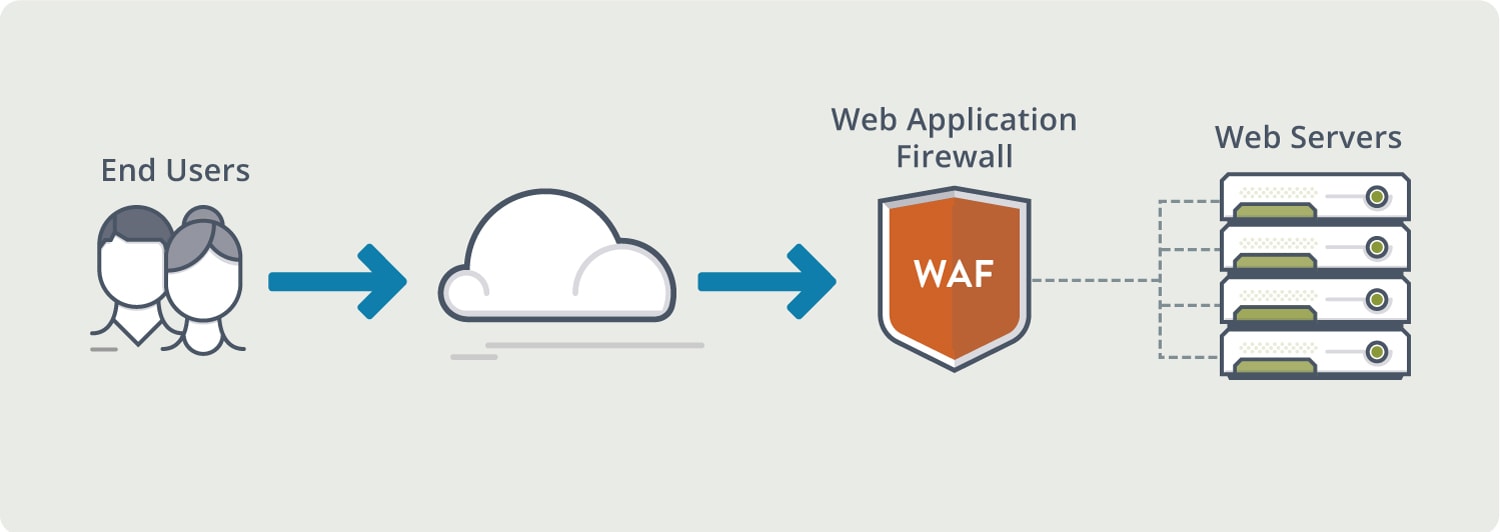
What Are Web Application Firewalls?
Web application firewalls assist load balancing by examining HTTP traffic before it reaches the application server. They also protect against web application vulnerability and unauthorized transfer of data from the web server at a time when security breaches are on the rise. According the the Verizon Data Breach Investigations Report, web application attacks were the most prevalent breaches in 2017 and 2018.
The PCI Security Standards Council defines a web application firewall as “a security policy enforcement point positioned between a web application and the client endpoint. This functionality can be implemented in software or hardware, running in an appliance device, or in a typical server running a common operating system. WAF security may be implemented using a stand-alone device or integrated into other network components.”
How Does A Web Application Firewall Work?
A web application firewall (WAF) intercepts and inspects all HTTP requests using a security model based on a set of customized policies to weed out bogus traffic. WAFs block bad traffic outright or can challenge a visitor with a CAPTCHA test that humans can pass but a malicious bot or computer program cannot.
WAFs follow rules or policies customized to specific vulnerabilities. As a result, this is how WAFs prevent DDoS attacks. Creating the rules on a traditional WAF can be complex and require expert administration. The Open Web Application Security Project maintains a list of the OWASP top web application security flaws for WAF policies to address.
WAFs come in the form of hardware appliances, server-side software, or filter traffic as-a-service. WAFs can be considered as reverse proxies i.e. the opposite of a proxy server. Proxy servers protect devices from malicious applications, while WAFs protect web applications from malicious endpoints.
What Are Some Web Application Firewall Benefits?
A web application firewall (WAF) prevents attacks that try to take advantage of the vulnerabilities in web-based applications. The vulnerabilities are common in legacy applications or applications with poor coding or designs. WAFs handle the code deficiencies with custom rules or policies.
Intelligent WAFs provide real-time insights into application traffic, performance, security and threat landscape. This visibility gives administrators the flexibility to respond to the most sophisticated attacks on protected applications.
When the Open Web Application Security Project identifies the OWASP top vulnerabilities, WAFs allow administrators to create custom security rules to combat the list of potential attack methods. An intelligent WAF analyzes the security rules matching a particular transaction and provides a real-time view as attack patterns evolve. Based on this intelligence, the WAF can reduce false positives.
What Is the Difference Between a Firewall and a Web Application Firewall?
A traditional firewall protects the flow of information between servers while a web application firewall is able to filter traffic for a specific web application. Network firewalls and web application firewalls are complementary and can work together.
Traditional security methods include network firewalls, intrusion detection systems (IDS) and intrusion prevention systems (IPS). They are effective at blocking bad L3-L4 traffic at the perimeter on the lower end (L3-L4) of the Open Systems Interconnection (OSI) model. Traditional firewalls cannot detect attacks in web applications because they do not understand Hypertext Transfer Protocol (HTTP) which occurs at layer 7 of the OSI model. They also only allow the port that sends and receives requested web pages from a HTTP server to be open or closed. This is why web application firewalls are effective for preventing attacks like SQL injections, session hijacking and Cross-Site Scripting (XSS).
When Should You Use a Web Application Firewall?
Any business that uses a website to generate revenue should use a web application firewall to protect business data and services. Organizations that use online vendors should especially deploy web application firewalls because the security of outside groups cannot be controlled or trusted.
How Do You Use a Web Application Firewall?
A web application firewall requires correct positioning, configuration, administration and monitoring. Web application firewall installation must include the following four steps: secure, monitor, test and improve. This should be a continuous process to ensure application specific protection.
The configuration of the firewall should be determined by the business rules and guardrails by the company’s security policy. This approach will allow the rules and filters in the web application firewall to define themselves.
Does VMware NSX Advanced Load Balancer Offer a Web Application Firewall?
Yes. The VMware NSX Advanced Load Balancer’s Web Application Firewall (WAF) delivers high-performance web application security with point-and-click simplicity. It enables customized policy configurations and helps achieve compliance with GDPR, HIPAA and PCI DSS. It simplifies security rules, minimizes false positives with advanced analytics and protects applications from DDoS attacks and OWASP Top 10 threats with real-time insights.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.
For more information on WAFs see the following resources: