TLS Proxy Definition
A TLS proxy is a gateway for a Transport Layer Security (TLS) connection, which is a protocol that provides communications security over a computer network. A TLS proxy server protects against denial-of-service (DoS) attacks and other security threats.
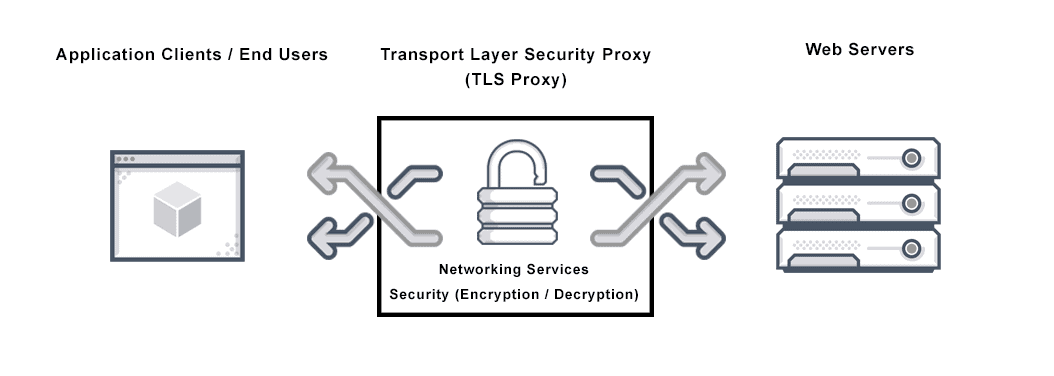
What is TLS Proxy?
A TLS proxy is used in secure connections to allow for additional networking services while protecting against denial-of-service attacks. TLS (Transport Layer Security) provides encryption and authenticity of communication over the Internet. It started out for secure online e-commerce transactions and has quickly become the defacto security protocol. TLS proxies are becoming more prominent than older SSL (Secure Socket Layer) proxies when it comes to handling incoming TLS connections.
How Does TLS Proxy Work?
A connection is being intercepted by a TLS proxy when it inspects incoming traffic to block malicious connections. A high speed redundant network is used to run the TLS proxy to protect against distributed DoS (DDoS) attacks.
Transport Layer Security (TLS) often uses an HTTP proxy to inspect the HTTP traffic between client and server. A TLS handshake session by itself does not offer protection. It only creates the connection. Security is enforced by running a TLS session between the client and the HTTP proxy along with a separate session between the HTTP proxy and the server.
Why Uninstall TLS Proxy?
There are times when uninstalling a TLS proxy is needed. Older SSL/TLS protocols can be a security risk. Outdated versions of SSL/TLS are susceptible to bugs that can allow attackers to decrypt communications.
Sometimes HTTPS certificate errors need to be bypassed because they are too sensitive and an over abundance of warnings can result in problematic false positives or false negatives.
The best way to prevent attacks is to configure the TLS proxy to remove all incoming HTTP headers that have the same name (header rewrite). The header should also have a name that is not commonly known, or something long and random.
How To Bypass TLS Proxy?
Enterprises wishing to modify traffic as they see fit can run into problems when applications stop to verify that every certificate of authority is valid. This can cause bottlenecks when trying to validate certificates. It’s necessary to convince an app that a certificate of authority is trusted and valid before being able to act as man-in-the-middle (MITM) and modify traffic flow. This requires bypassing the TLS proxy with the following techniques:
• Add a custom certificate of authority (CA) to the trusted server certificate store
• Overwrite a packaged CA with a custom CA
• Reverse custom certificate code
Does Avi offer TLS Proxy?
Yes. Avi can serve as a TLS proxy for the back-end servers in the service’s pool. It communicates with the client over SSL/TLS.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.
For more information see the following TLS proxy resources: