Bot Detection Definition
Bot detection prevents scripted attacks by identifying when a request is likely to be originating from a software program (a bot).
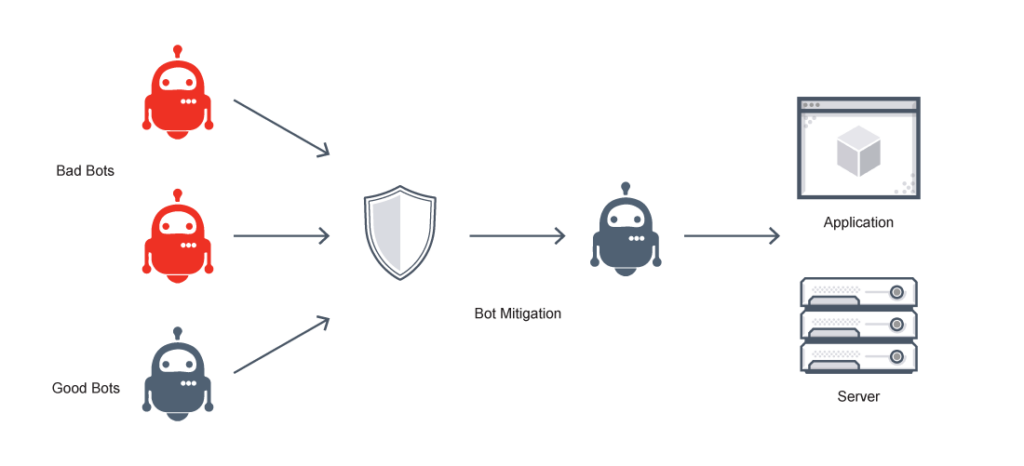
The bot detection process identifies non-human IP addresses and devices that are controlled by automation, such as web scraping. Bot detection software and other bot detection tools achieve this through device integrity checks, pattern recognition, behavior analysis, and by examining characteristics such as the user agent, IP reputation, and origin network (autonomous system number).
A bot detection framework mitigates attacks without hampering the use of legitimate users. When a bot detection system catches such an attack, it can display a CAPTCHA step or otherwise interrupt the login process to eliminate scripted and bot traffic.
Bot Detection FAQs
What is Bot Detection?
Bot detection software identifies bad bots to prevent threats and hacking. Typically, this kind of software uses a bot detection algorithm to detect unusual activity. Bot detection requires strong client-side and server-side connections. The client-side connection reveals a contextual layer in real-time. The server-side connection reveals contextual datasets from session activity.
Bot detection solutions identify whether a user is a human using patterns in real-time data. Bot detection sees unusual activities and patterns and prevents them from accessing user data or jeopardizing safety.
How Do Bots Attack?
Good bots are designed to run autonomously, completing repetitive tasks quickly. But so are bad bots, and this empowers cybercriminals and fraudsters who no longer need to replicate the same actions millions of times. Instead, they rely on bots or chains of malware-infected computers: botnets.
While it may appear that bot attacks are very easy to detect, in truth most hackers know how to avoid bot detection with a fairly high degree of sophistication. So what is the primary challenge of bot detection and blocking?
Specific threat models include:
Inventory hoarding. Bad bots might hoard inventory in online shopping carts, both keeping it unavailable to legitimate users and confusing things like fees and commissions. Or, an attacker might attract advertisers to a fake website so bad bots can click on the company’s ads and create accounts to buy inventory. This kind of account creation allows attackers to resell products at a profit. This is how ticket scalping works, for example.
App spoofing. Mobile application spoofing involves deploying a malicious mobile app to mimic the visual appearance of a highly trafficked app to send false engagement signals and useless bot clicks.
Account takeover (ATO). This automated threat allows bad actors to gain access to online accounts, usually via bot-driven attacks, such as credential cracking or stuffing. Account takeover can result in data leaks and reputational harm.
Other Use Cases for Automated Bot Detection:
- DDoS attacks
- Phishing attacks
- Brute force attacks/credential stuffing
- Fake reviews / posts / comments
- Scraper bots
- Marketing fraud
Bots attack three main channels:
API bot detection. The most common route of attack for bots is via application programming interfaces or APIs. APIs allow systems, mobile devices, and computers to communicate. Malicious bots mimic real users to hack into these communications and access the system.
Mobile Apps. Mobile apps are highly vulnerable and the most hacked channel for bots. Security is less effective overall on mobile apps, but they still hold critical financial and personal data.
Websites. Websites are a common location for bot activity. Bot activity on websites includes scraping and login attempts, for example.
Bot mitigation on all three channels is essential to protecting any organization from bad bots.
Bot Detection Techniques
Here are some common bot detection and bot mitigation techniques:
Captcha. A Captcha challenge is the most common way to prevent bad bots. However, Captcha isn’t particularly effective for detecting bots. Overall and used alone, these are a less effective way to prevent bots from scraping information, accessing websites, or hacking systems.
Invisible challenges. Invisible challenges verify that traffic originates with a legitimate user and not with a bad bot. Invisible challenges make automated attacks too expensive to conduct using a cryptographic proof-of-work in-order which increases their difficulty exponentially.
Manual blocking. Manual bot mitigation is possible—but slow and difficult. This kind of bot detection is best as an interim measure.
Fake data. Feeding fake data to a bad bot on your system can in some cases prevent the attack from accessing the information they want—but this is a temporary solution as advanced bots are more likely to discover fake data.
Bot detection techniques vary, but some features are usually present:
Device fingerprinting. Analyzing hardware and software that connect to the site to identify suspicious activity including botnets using spoofing tools.
IP analysis. Analyze the site’s online connection to allow human website visitors and filter out bots.
Real-time alerts. Create fraud alerts and address traffic spikes that point to a botnet attack.
Velocity risk rules. In the context of bot detection, velocity rules reveal how often users take actions online, offering insights into human behavior and motivation, and helping identify bots that perform repetitive sequences or actions.
Bot Detection Software and Other Bot Detection Tools
Bot detection and mitigation software allows legitimate traffic through, identifies bad bots, and blocks them. In general, the best bot detection software platforms should do several things well:
- Monitor. It should constantly monitor networks, websites, and applications.
- Classify. It should detect bots, classify them appropriately, and identify all malicious bot activity.
- Block/manage. It must take the correct actions to prevent access and malicious actions from bad bots and botnets while allowing access to legitimate bots and human users.
Automated bot detection and fraud prevention systems use a set of risk rules to detect suspicious bot activity, either for human review or automatic blocking. They examine various characteristics to determine whether traffic originates with a person or a bot, such as the network of origin (autonomous system number), the user agent, and the IP reputation.
Ideally, bot detection systems are either modular or customizable to permit greater flexibility and control over how the pipeline handles traffic. Ideally, organizations can customize classifications to describe known bots for more appropriate management.
Bot classification includes the creation and control of security policies to govern each type of bot, from good to malicious. Good bots include the search engine crawlers the organization relies upon for organic traffic, and the system might also identify custom bots, or even some bots with status that remains unknown, without enough data to decide. Bad bots might include click fraud bots or scrapers, and dangerous bots include botnet attackers or those who impersonate humans. And although humans should remain the majority of traffic throughout this process, bots will probably make up about 40% of traffic monitored.
The bot management pipeline is the locus for taking action on bots. These might include permitting or allowing the bot traffic to reach its destination in the application security stack, or denying it and closing or dropping the connection before it can reach it. Other actions include rate-limiting or allowing the connection up to a set threshold, or other custom responses such as those set by time of day or based on conditions.
Why Use Bot Detection?
Why use specific bot detection companies or bot detection tests instead of a WAF—or is a WAF bot detection? Bot detection has specific advantages, especially for organizations at high risk:
Real-time detection. A bot detection solution offers real-time detection. Not limited to office hours or when staff are available, a bot detection system protects the business around the clock. Bot detection assesses signals in real-time night and day, no matter who is physically active, and blocks them immediately.
Save money and time. Bot detection is affordable yet it secures financial details and protects data from bad bot activity without human labor around the clock.
Increase performance. Bad bots hamper speed on any website. Bot detection and blocking enables complete inventory and a website with faster speed and capacity. This boosts engagement and conversion rates and reduces visitor bounce rates.
Prevent data breaches. Malicious bots can steal, transmit, and pollute data worldwide. The best bot detection tools can reduce or prevent these data breaches.
Does VMware NSX Advanced Load Balancer Offer Bot Detection?
Yes. The VMware NSX Advanced Load Balancer bot management platform consists of three main steps, and the first of those is bot detection. Bot detection is the first and most crucial step in the pipeline.
In this step, each bot detector—or decision component—characterizes the request with some amount of information. Decision components include IP reputation, IP location, and user-agent.
Bot detection and management is a crucial, fully integrated layer of the application security stack that includes a WAF, DDoS protection, application rate limiting, AV malware protection, user authentication, encryption plus L3/4 and L7 ACLs. It works across hybrid- and multi-cloud environments, including private clouds, on-premises, and public clouds, just like the rest of the application services platform.
Learn more about bot detection and bot management with VMware NSX Advanced Load Balancer here.
For more on the actual implementation of load balancing, security applications and web application firewalls check out our Application Delivery How-To Videos.