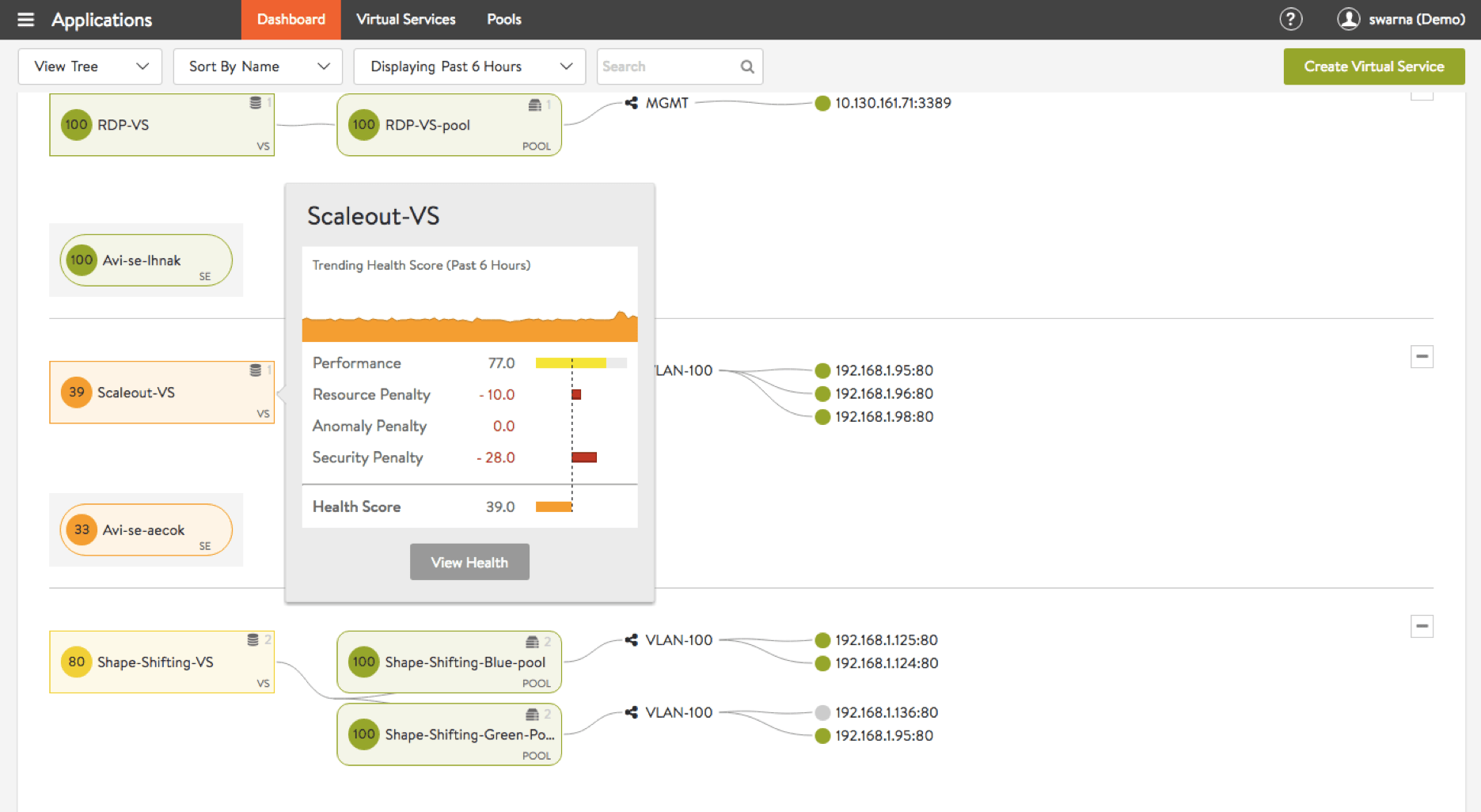
Avi summarizes analytics information into a handy Health Score that provides a quick snapshot of the overall applications. Health Score is determined by:
Actionable Analytics From Your Load Balancer
Load balancers occupy a privileged position, in-line with applications in the enterprise network. However, legacy, appliance-based load balancers do not leverage their position to provide real-time insights. Avi’s software-defined architecture delivers unprecedented analytics using continuous insights collected by the load balancers.
Architected for APM-like Analytics
The Avi Service Engines provide a distributed load balancing fabric collecting millions of data points in real time. The real-time telemetry is processed by the Avi Controller continuously, to provide unprecedented visibility and application insights (that complement Application Performance Monitoring tools). It enables network engineers and developers to get actionable insights into application performance, security, and end-user experience simplifying troubleshooting down to minutes.
Actionable Analytics
APPLICATION PERFORMANCE
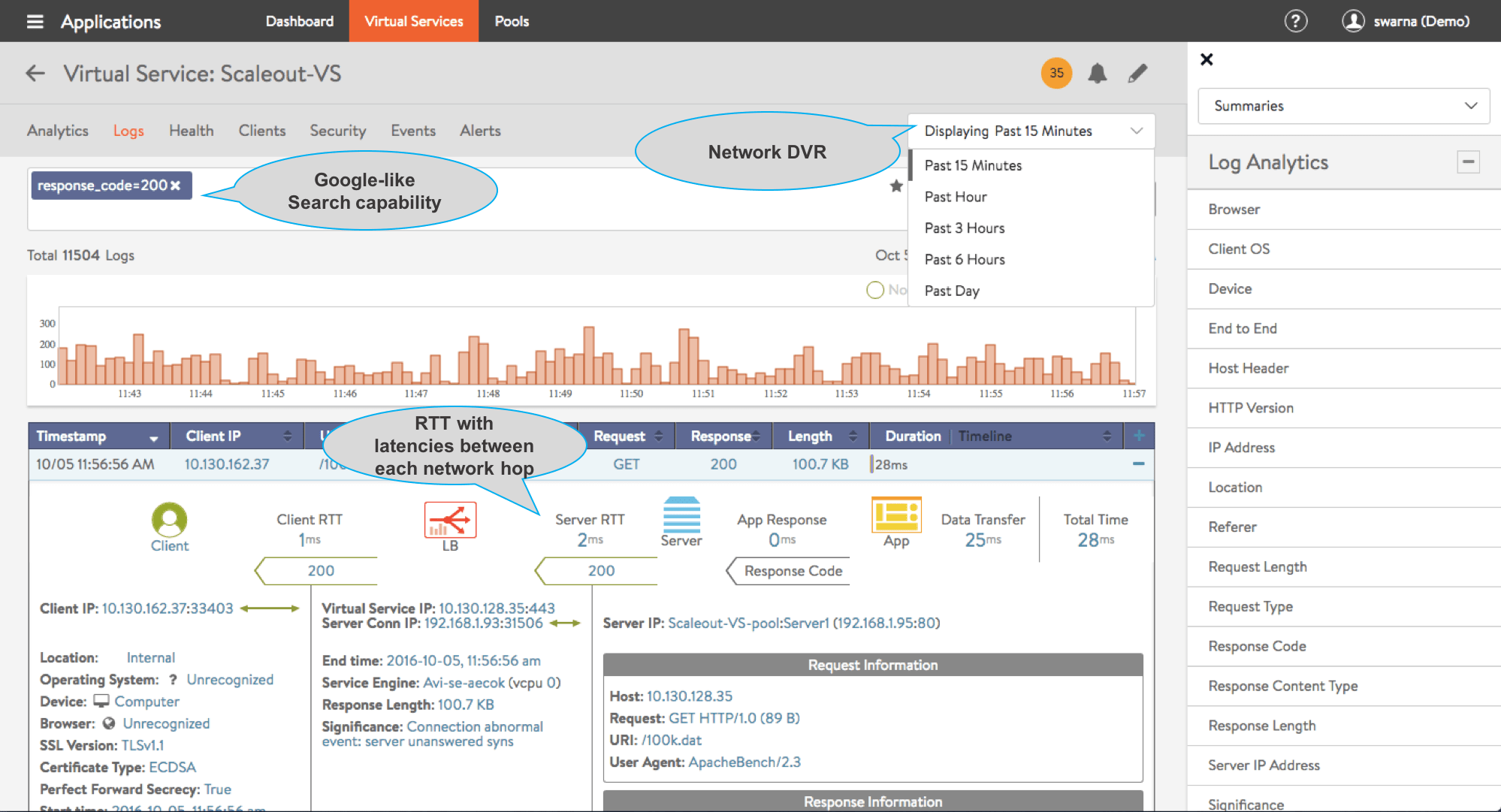
- Troubleshoot application issues in less than a minute
- End-to-end round trip times with latencies between each network hop
- “Network DVR” like capability to record-and-replay specific transactions
- Google-like search filters transactions based on device, location, errors, etc.
SECURITY
- Actionable insights into security issues and DDoS attacks
- Highlights potential risks with SSL certificates and TLS versions used
- Quick snapshot of the overall security posture
END USER EXPERIENCE
- Granular visibility into end user experience and server response in real time
- End-to-end timing for each transaction to help solve end-user experience issues
- Empowers application owners with end user stats to optimize and improve apps