Avi Web Application Firewall
Web application firewalls (WAFs) are intended to protect businesses from web app attacks and proactively prevent threats.
Traditional web application security solutions do not provide visibility and security insights that administrators can use to create an effective application security posture. Enterprises need real-time visibility into application traffic, user experience, security and threat landscape, and application performance to identify and protect against the most sophisticated attacks.
Avi Vantage leverages software-defined architecture and its strategic location on the network to gain real-time application insights. The built-in WAF solution provides application security and networking teams with an elastic and analytics-driven solution that scales and simplifies policy customization and administration through central management.
Avi Vantage provides a script called avi-iwaf-vpatch.py that imports DAST scanner results. The imported results are used to construct a WAF Policy that protects from the security threats found by the scanner. The technique is often called virtual patching.
Avi WAF plays an integral role in a defense-in-depth strategy that does comprehensive threat analysis, mitigates risk, provides zero-day protection against unpublished exploits and optimizes application security.
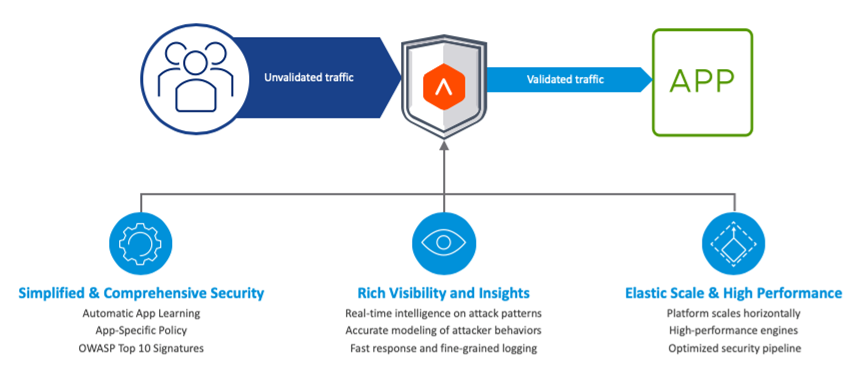
Avi WAF is built on the core design principles shown below to ensure that WAF is a simple yet comprehensive security solution.
The following table provides a comprehensive list of links to documentation for WAF in Avi Vantage:
| Documentation | Title |
|---|---|
| Configuring WAF on Avi Vantage | Configuring iWAF |
| Configuring WAF Policy | WAF Policy |
| Configuring Whitelist rules | WAF Policy Whitelist |
| Configuring Positive Security rules | Positive Security |
| Configuring CRS Rules | WAF Policy Signatures |
| Enabling mode delegation for WAF policy | Mixed Mode for WAF Policy |
| Analyzing WAF logs and WAF metrics | Monitoring iWAF |
| Sizing Metrics | Metrics for iWAF Sizing |
| Configuring anomaly scoring in mode | iWAF in Anomaly Scoring Mode |
| Configuring WAF exceptions with regex matching for arguments | Regex Matching for Arguments |
| Handling large uploads | Upload Handling in WAF |
| Configuring WAF geoIP transformations | GeoIP Transformations |