iWAF in Anomaly Scoring Mode
Overview
WAF Policy can be configured to operate in either detection only or in enforcement mode by default. Here, the policy flags or rejects a request based on the match of a rule.
Alternatively, the anomaly scoring mode can be used.
This article explains how anomaly scoring mode works.
Anomaly Scoring
All the rules that match add up to a request-based threshold. If that threshold is reached, the request will be blocked.
Within the Service Engine, by default, multiple thresholds are set and can be changed.
Default thresholds
setvar:tx.sql_injection_score_threshold=15,
setvar:tx.xss_score_threshold=15,
setvar:tx.rfi_score_threshold=5,
setvar:tx.lfi_score_threshold=5,
setvar:tx.rce_score_threshold=5,
setvar:tx.command_injection_score_threshold=5,
setvar:tx.php_injection_score_threshold=5,
setvar:tx.http_violation_score_threshold=5,
setvar:tx.trojan_score_threshold=5,
setvar:tx.session_fixation_score_threshold=5,
setvar:tx.inbound_anomaly_score_threshold=5,
setvar:tx.outbound_anomaly_score_threshold=4
The most frequently used threshold is inbound_anomaly_score_threshold, which is used to deny in the default CRS rule 949110 - inbound anomaly score.
setvar:tx.critical_anomaly_score=5,
setvar:tx.error_anomaly_score=4,
setvar:tx.warning_anomaly_score=3,
setvar:tx.notice_anomaly_score=2"
When the iWAF policy is executed, rules that match are adding their match value to the specific thresholds:
For example, 931120. Check for RFI (3/4).
setvar:tx.anomaly_score=+%{tx.critical_anomaly_score}
setvar:tx.rfi_score=+%{tx.critical_anomaly_score}
Finally, when all rules are evaluated, the rule 949110 - inbound anomaly score will check the threshold tx.anomaly_score and trigger a deny if it was reached.
SecRule TX:ANOMALY_SCORE "@ge %{tx.inbound_anomaly_score_threshold}"
"msg:'Inbound Anomaly Score Exceeded (Total Score:
%{TX.ANOMALY_SCORE})', severity:CRITICAL, phase:request,
id:949110, t:none, deny, log, tag:'application-multi',
tag:'language-multi', tag:'platform-multi', tag:'attack-generic',
setvar:tx.inbound_tx_msg=%{tx.msg},
setvar:tx.inbound_anomaly_score=%{tx.anomaly_score}"
A log file entry is created.
To view the log,
- Navigate to Applications > Virtual Services.
- Click on the virtual service mapped to the WAF policy.
- Click on Logs.

Setting Up iWAF in Anomaly Scoring mode
Changing the Default Behaviour of iWAF Profile
Note: A rule can have different disruptive actions. Most of the rules use block as the disruptive action. Block will trigger the rule engine to execute the default action mentioned in the iWAF profile attached to the policy. This default action contains the deny action that will then trigger the flag (detection) or reject (enforcement) of the request.
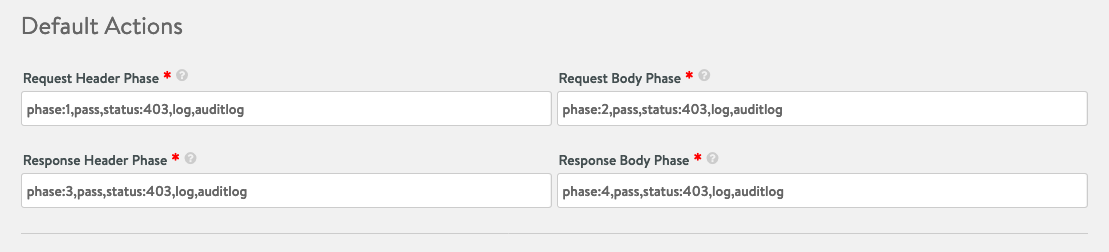
For example,
Default Action: phase:1,pass,status:403,log,auditlog.
Therefore, the new default action needs to be pass. It needs to be changed for all phases of the iWAF handling.
To modify the default action,
- From the Avi UI, navigate to Templates > WAF > WAF Profile.
- Click on the edit icon against the required policy.
- Modify the Default Actions in the Edit WAF Profile: screen as shown below:
Changing individual thresholds and blocking of different threshold variables (by group, for example)
Every threshold or score variable can be changed by using a pslackre-CRS custom rule:
SecRule REMOTE_ADDR "@unconditionalMatch"
"id:4099803,phase:1,pass,setvar:tx.rfi_score_threshold=2"
For blocking by using different thresholds, a custom Post-CRS rule is required.
Note: It is recommended to disable the CRS rule 949110, which denies the request on the overall score.
This rule is a good example for the blocking rule.
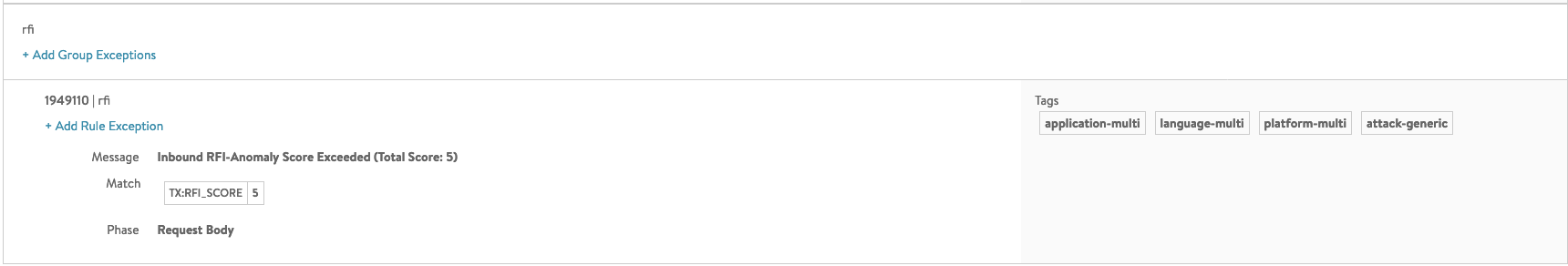
SecRule TX:RFI_SCORE "@ge %{tx.rfi_score_threshold}" "msg:'Inbound
RFI-Anomaly Score Exceeded (Total Score: %{tx.rfi_score})',
severity:CRITICAL, phase:request, id:1949110, t:none,
deny, log, tag:'application-multi', tag:'language-multi',
tag:'platform-multi', tag:'attack-generic',
setvar:tx.inbound_tx_msg=%{tx.msg}"
This rule blocks only on the tx.rfi_score_threshold and the accumulated tx.rfi_score variable.
Similar rules can be created for all other groups of attacks.
Caveat
Note that in the ModSecurity language, the variable (for example, TX:RFI_SCORE) to be written with a “:” (colon).
In the Actions list and in the Operator, it is written using a . (dot). (For example, tx.rfi_score)
If this is not done correctly, the rule will not match as intended.
Sample Test Case
Create any request with the ARGS payload, for example, https://abc-eval-test.net/am-test
This will trigger 931120. Check for Remote File Inclusion (3/4) as shown below: